
Contents
Supported Authentication Methods
Civil Pro supports the following methods of authentication:
- Civil Pro Identity – civil pro’s own internal username/password
- Google Identity
- Microsoft Identity (azure AD)
- Microsoft Identity (office 365)
Civil Pro uses Google Firebase as the broker for all authentication methods except Civil Pro Identity. SSO is for authentication only, all authorization is managed by the Civil Pro application internally.
NOTE: To use Microsoft Azure AD for single sign on, your system administrator must set the Civil Pro application up as an authorized application in your AD account. Contact us for instructions
Controlling Authentication Methods
The authentication methods available to users can be controlled by subscription settings. By default, all authentication methods are enabled. In addition to controlling individual methods, it is possible to disable Civil Pro authentication only for users with SSO, and it is also possible to disable Civil Pro authentication for specific users in the Users settings.
To control authentication in the desktop access Subscription Operations => Settings => Cross Project Settings
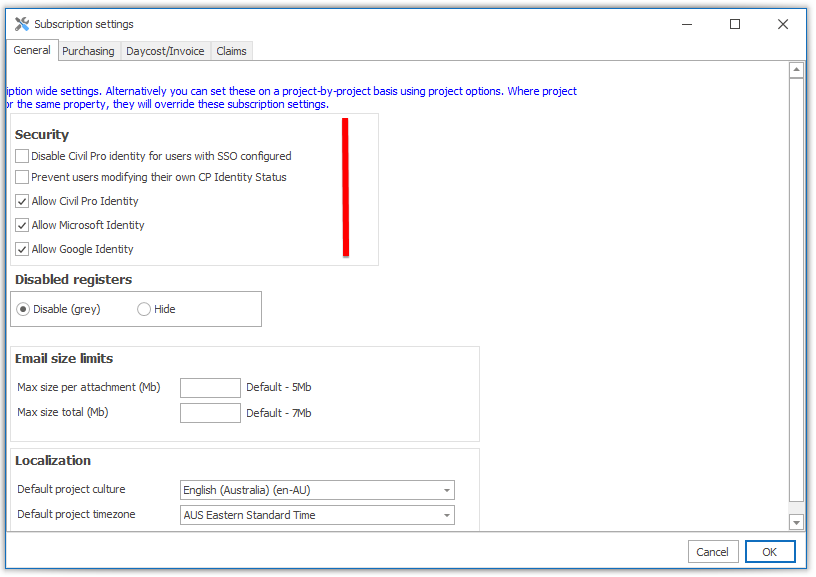
- Allow Civil Pro Identity – allow users to log on with a civil pro registered username and password
- Microsoft Identity – allow users to log on with an Office 365 or Azure AD Identity
- Google Identity – allow users to log on with Google Identity
- Disable Civil Pro Identity for users with SSO configured – when enabled, user accounts that have SSO registered against them cannot log on using Civil Pro Identity. This is useful for reducing the exposure for accounts that may have low quality passwords.
- Prevent users modifying CP Identity Status – Civil Pro supports a switch in the user register that disables the Civil Pro identity on a per-user basis. This is useful (for example) where you may enforce SSO for your internal resources, but allow Civil Pro Identity for external collaborators that have limited access to data.
How SSO is connected to Civil Pro roles
SSO in civil pro uses Google’s Firebase as a broker for authentication. All authorization is managed by Civil Pro. For this reason there will always be a Civil Pro user account for every user, even if they use SSO.
There are three ways SSO can be configured for a user
- Using the Invitiation process. If the user accepts the invitation using SSO, the account will be configured for SSO only
- A subscription Administrator creates the account with a Civil Pro Identity where the username matches the username expected from the SSO authentication (e.g. johnd@myco.com). When the user authenticates using their SSO identity, the automatching feature will associate the SSO identity with the user providing the pre-requisites are satisfied.
- A subscription administrator creates the account with a Civil Pro Identity. The user logs on with the CP Id and users the User Detail => Profile page to add SSO to their own account. SSO can also be removed this way unless prevented by subscription settings.
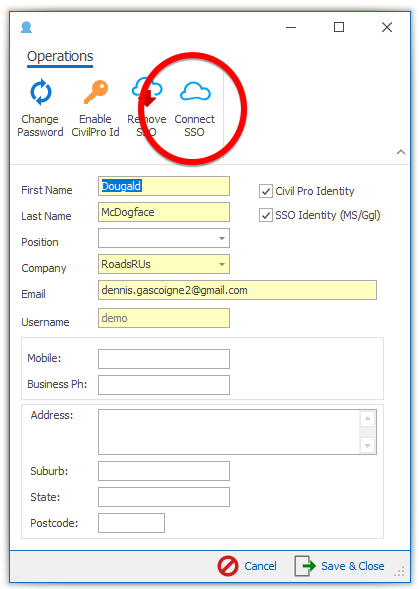
SSO Identity Automatching
When a user logs in with SSO, the following process occurs:
- The SSO provider’s login is launched
- Upon successful authentication, the unique ID is returned to Civil Pro
- Civil Pro attempts to match the Firebase ID against the Firebase IDs already connected to Civil Pro user accounts. If successful, the user is authorised and logged in
- If step 3 was unsuccessful, Civil Pro retrieves the email address from the SSO Identity. If this can be uniquely matched to a single user, then the Firebase Id is saved against the user and the user is authorised and logged in.
- If step 4 was unsuccessful, it is repeated using the email field for the user instead of the username field.